The Evolution of Cyber Risk: Three Trends Affecting Businesses
These three trends are exposing security vulnerabilities, and heightening the call for businesses to stay informed on the ways in which cybercriminals are adapting and advancing their operations.
Cybersecurity is one of the most prevalent risks in our hyper-connected society.
Due to the nature of technological advancements and the speed with which data can be manipulated, businesses and governments are seemingly trapped in a never-ending cycle of playing catchup as cybercriminals launch new and more sophisticated threats.
In the latest chapter of this evolution, cybercriminals are utilizing emerging technology and shifting their focus to different targets to carry out their malicious activities.
A New Approach to Data Ransom
Cybercriminals have long focused on encrypting their targets’ systems or data for ransom.
In response, many businesses have prioritized robust backups from which their data can be restored in the event of a ransomware attack.
This has forced cybercriminals to pivot in their approach to cash in on victims’ data.
Cybercriminals are now increasingly stealing highly sensitive data, often opting to forego system encryption, and instead threatening to publicly leak or sell this information on the dark web unless the organization pays up.
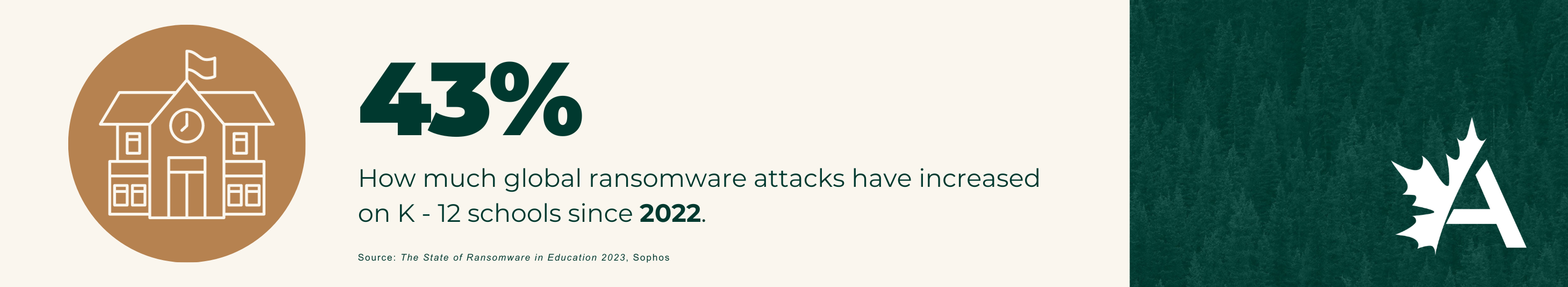
To get the most bang for their buck, cybercriminals are attacking the public sector more often as the government, healthcare and education industries house a wealth of private and confidential data. Furthermore, these industries tend to have restricted budgets and legacy systems, making them easy targets.
This doesn’t mean the private sector is off the hook — any organization that collects and stores data is at risk of a ransom attack.
New Technology Brings New Risks
The constant evolution of technology is a double-edged sword.
For example, many businesses are turning to current advancements like artificial intelligence (AI) to increase efficiencies; this technology is being used for the same purpose in the criminal world.
Cybercriminals have successfully worked around the built-in legal safeguards to use AI software to ramp up their production of malware and credible phishing emails.
They are also capitalizing on the mass interest in AI applications, such as ChatGPT, by creating fake websites purporting to offer AI software in order to steal credentials or launch malware.
AI can also be used to create voice clones to scam employees. For example, cybercriminals used AI to impersonate the boss of a UK-based energy firm to successfully steal $234,000 USD.
The future potential of quantum computing is another emerging risk as current cybersecurity and encryption technology is not adequate to guard against these sophisticated and powerful capabilities.
In response, cybersecurity stakeholders and experts are calling for organizations — particularly those involved in critical infrastructure — to start creating a quantum-readiness roadmap, which includes examining their vendors’ roadmaps.
This brings us to our third trend.
The Third-Party Connection
Increasing efficiencies often contributes to greater success for both businesses and cybercriminals.
As such, businesses often contract out various cyber services where it is cost-effective, and these third-party vendors — such as those who provide payment processing, software, IT and marketing services and products — are increasingly coming under attack.
Cybercriminals can wreak extensive havoc by targeting and exposing the vulnerabilities of third-party vendors; targeting one service provider can spread malware to users all along the network supply chain, hitting several targets from which to extort payment from or steal data.
This affects not only the businesses who use impacted third-party vendors, but also those businesses’ contacts.
Recent examples of this include attacks that targeted MOVEit, a popular file-sharing software, which compromised the data of over 600 businesses worldwide, impacting over 40 million people; and Log4J, a widely used logging library software, which saw more than 100 hacking attempts occur every minute at the height of the exploitation.
Businesses can no longer be complacent in ensuring their own systems are adequately protected. They also have a responsibility to review and ensure their third-party providers subscribe to a high level of cybersecurity.
This is a very challenging space to monitor. As more businesses rely on third-party vendors, these providers are increasingly being inundated with compliance requests and may be reluctant to fully open their systems up to scrutiny.
How Are Businesses to Respond?
Cybersecurity will always be fluid.
The key to effectively adapting in response to criminal activities remains education — businesses must be vigilant in staying informed about escalating and emerging threats as well as current best practices for cybersecurity. This should not be done in silos, but instead include the sharing of information between stakeholders, vendors and staff.
Ongoing training of employees — who remain the weakest link when it comes to a business’ cybersecurity defences — is paramount, as does the routine reviewing, testing and updating of response plans.
Budgets should also reflect the increased need for IT expertise, cybersecurity and cyber liability insurance.
Hillaine McCaffrey is a Senior Underwriter & Broker, D&O and Cyber, with Acera Insurance (formed through the merger of several award-winning brokerages, including Rogers Insurance, CapriCMW and Megson FitzPatrick). She specializes in providing insurance and risk management solutions related to cybersecurity and directors and officers. Hillaine has a law degree (University of Calgary, JD’96) in addition to her Canadian Risk Management (CRM) and Chartered Insurance Professional (CIP) designations. She is licenced in Alberta, British Columbia, Manitoba, New Brunswick, Newfoundland, Ontario, Prince Edward Island, Saskatchewan and the Yukon.